Abandoned Object Detection

Algorithm Introduction
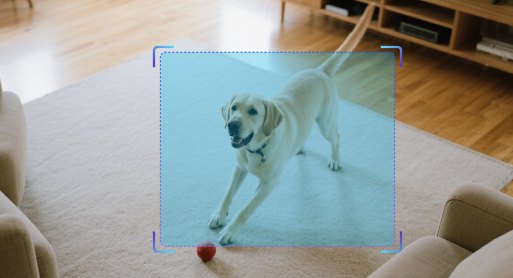
The abandoned object detection algorithm is designed to identify suspicious objects lingering in predefined security zones during designated time periods, triggering alarms when objects exceed preset dwell time thresholds. The system outputs the initial detection timestamp, captured images of the lingering object, and 2D bounding boxes across all relevant video frames.
Operational requirements:
Operational requirements:
- ● Lighting conditions:
- Primary applicability: Indoor environments, daytime outdoor scenes, and evening/night scenes with clear object visibility
- ● Limitations affecting detection accuracy:
- - Severe nighttime illumination deficiency
- - Excessive movable interference objects within ROI (e.g., flowing curtains, fluttering papers)
- - High pedestrian traffic or prolonged human presence (recommended maximum 2 persons in ROI)
- - Tracking interruptions may occur when lingering objects are obscured by moving objects/pedestrians for >4 seconds
- ● Camera positioning requirements:
- - Unobstructed visibility of ROI areas
- - Minimal risk of occlusion by pedestrians or interference objects
- ● Image quality standards:
- - No significant motion blur or imaging noise
- - Stable camera mounting without vibrations
- ● Object resolution requirements:
- - Minimum object diameter >20 pixels
- - (OR) Lingering objects should occupy ≥5% of ROI area
Application Value
-

Public Transport Safety
The algorithm monitors for abandoned packages at subway and train stations to prevent explosive threats. It also detects malfunctioning vehicles or fallen cargo on highways to reduce the risk of traffic accidents. -

Power Facility Protection
Recognizes foreign objects such as kites and plastic films on transmission lines to prevent short circuits. -

Critical Area Security
Monitors suspicious object abandoned in airport restricted areas and bank lobbies to support post-event evidence collection. -

Smart Construction Site Management
Detects uncleared construction waste or improperly stacked materials in work zones.
FAQ
-
Algorithm AccuracyAll algorithms published on the website claim accuracies above 90 %. However, real-world performance drops can occur for the following reasons:
(1) Poor imaging quality, such as
• Strong light, backlight, nighttime, rain, snow, or fog degrading image quality
• Low resolution, motion blur, lens contamination, compression artifacts, or sensor noise
• Targets being partially or fully occluded (common in object detection, tracking, and pose estimation)
(2) The website provides two broad classes of algorithms: general-purpose and long-tail (rare scenes, uncommon object categories, or insufficient training data). Long-tail algorithms typically exhibit weaker generalization.
(3) Accuracy is not guaranteed in boundary or extreme scenarios.
-
Deployment & InferenceWe offer multiple deployment formats—Models, Applets and SDKs.
Compatibility has been verified with more than ten domestic chip vendors, including Huawei Ascend, Iluvatar, and Denglin, ensuring full support for China-made CPUs, GPUs, and NPUs to meet high-grade IT innovation requirements.
For each hardware configuration, we select and deploy a high-accuracy model whose parameter count is optimally matched to the available compute power.
-
How to Customize an AlgorithmAll algorithms showcased on the website come with ready-to-use models and corresponding application examples. If you need further optimization or customization, choose one of the following paths:
(1) Standard Customization (highest accuracy, longer lead time)
Requirements discussion → collect valid data (≥1 000 images or ≥100 video clips from your scenario) → custom algorithm development & deployment → acceptance testing
(2) Rapid Implementation (Monolith:https://monolith.sensefoundry.cn/)
Monolith provides an intuitive, web-based interface that requires no deep AI expertise. In as little as 30 minutes you can upload data, leverage smart annotation, train, and deploy a high-performance vision model end-to-end—dramatically shortening the algorithm production cycle.